Objective
Configure a SonicWall Router using the new interface.
The purpose of this article is to provide a sample configuration. At the time of article creation, this device was in a known working state on the firmware used.
Keep in mind different firmware versions will interact with hosted VoIP services in different ways. While this device may be fully functional on the tested or current firmware version, it is possible newer revisions will cause disruptions in service or make a device fully compliant with the required settings for hosted VoIP services where it was previously not.
Keep in mind different firmware versions will interact with hosted VoIP services in different ways. While this device may be fully functional on the tested or current firmware version, it is possible newer revisions will cause disruptions in service or make a device fully compliant with the required settings for hosted VoIP services where it was previously not.
Note: Tests indicate that QoS does not seem to work when Address object types are set as FQDN. (Conversely, the Host, Range, or Network types seem to work just fine.) The TZ100, in particular, exhibits high traffic security.
Applies To
- SonicWall Routers
Procedure
Administrative Information
- Make sure your router is powered on and connected to your network.
- In a browser on a computer on the same network as the router, navigate to the following IP address: 192.168.168.168 (X0).
- Log in (default credentials shown below).
- Username: admin
- Password: password
Tested on the following firmware versions:
- Fimware version 6.5.x.x and later
Adding/editing 8x8 subnets is recommended when available. See X Series Technical Requirements.
Note: We highly recommend consulting an IT or network professional when configuring advanced network settings or devices. NAT issues causing duplicate ports have been reported for firmware version 6.2.3.x. It is not recommended to use this firmware version.
Firewall Configuration
- Creating Service (port) objects/groups to cover signaling/media seems to produce results just as good as the Edgewater routers.
- Creating Address (IP Address) objects/groups to cover signaling/media also works well as long as the type of the object is set to Host, Range, or Network. There appears to be a bug where FQDN does not improve call quality due to the router being unable to resolve DNS SRV records.
Disable Consistent NAT and SIP Transformations
Note: The TZ400 is an exception to this requirement. For the TZ400 model, Consistent NAT should be enabled.
Additional information on the "Consistent NAT" setting can be found below under Known Issues.
- Go to VoIP > Settings.
- Uncheck the boxes next to Enable Consistent NAT and Enable SIP Transformations.
Disable Stealth Mode and RTSP
- Go to Firewall Settings > Advanced.
- Uncheck the boxes next to Enable Stealth Mode and Enable RTSP Transformations.
Add 8x8 Subnets
- Go to Objects > Address Objects.
- Click Add.
- Add each 8x8 subnet one at a time.
8x8 subnets for Sonicwall:
West 1
192.84.16.0/22
255.255.252.0
West 1
192.84.16.0/22
255.255.252.0
West 2
162.221.236.0/23
255.255.254.0
162.221.236.0/23
255.255.254.0
West 3
8.5.248.0/23
255.255.254.0
8.5.248.0/23
255.255.254.0
West 4
63.209.12.0/24
255.255.255.0
63.209.12.0/24
255.255.255.0
East 1
8.28.0.0/22
255.255.252.0
8.28.0.0/22
255.255.252.0
East 2
162.221.238.0/23
255.255.254.0
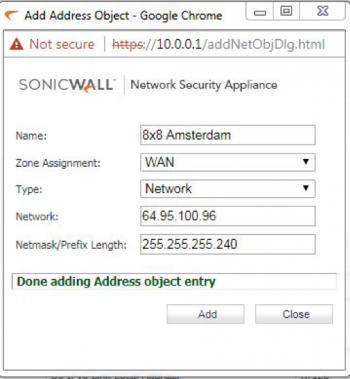
(One example shown.)
162.221.238.0/23
255.255.254.0
(One example shown.)
- Click the Address Groups tab.
- Click Add.
- Name the group 8x8 Subnets.
- Add each 8x8 subnet.
- Click OK.
Set Up Access Rules
- Go to Firewall > Access Rules.
See the screnshots below to follow the next steps:
- Click Add.
- Configure the General, Advanced, and QoS settings.
- Set the UDP time out to 660 seconds, if the TCP time out is less than 11 minutes, change the TCP time out to 11 minutes.
- Ensure Disable DPI is checked.
- Click OK.
Known Issues
- SonicWall TZ400/TZ500 requires Consistent NAT to be on. The exception to this would be if the TZ400 is on firmware version SonicOS Enhanced 6.2.5.3-35n. With this firmware version, disable Consistent NAT.
- Firmware version 6.2.3.x causes Duplicate UDP ports regardless of NAT settings.
- Firmware version 6.2.7 has DPI (deep packet inspection) under access groups on NSA series, which causes Call Quality issues despite rules added in.
- Firmware version 6.2.7.x (and higher): 802.1p tagging breaks phone connectivity.
- Additional testing has found that the "Consistent NAT" setting may need to be toggled depending on the firmware version in use. It may be necessary to toggle this setting on or off depending on the issues being experienced and then testing for stability.
- The following SonicWall models and firmware versions require Consistent NAT turned ON: SonicOS NSA 2600 Enhanced 6.2.2.1-14n (device needs to be restarted in order for the setting to stick).


